How Does Our DDoS Protection Work?
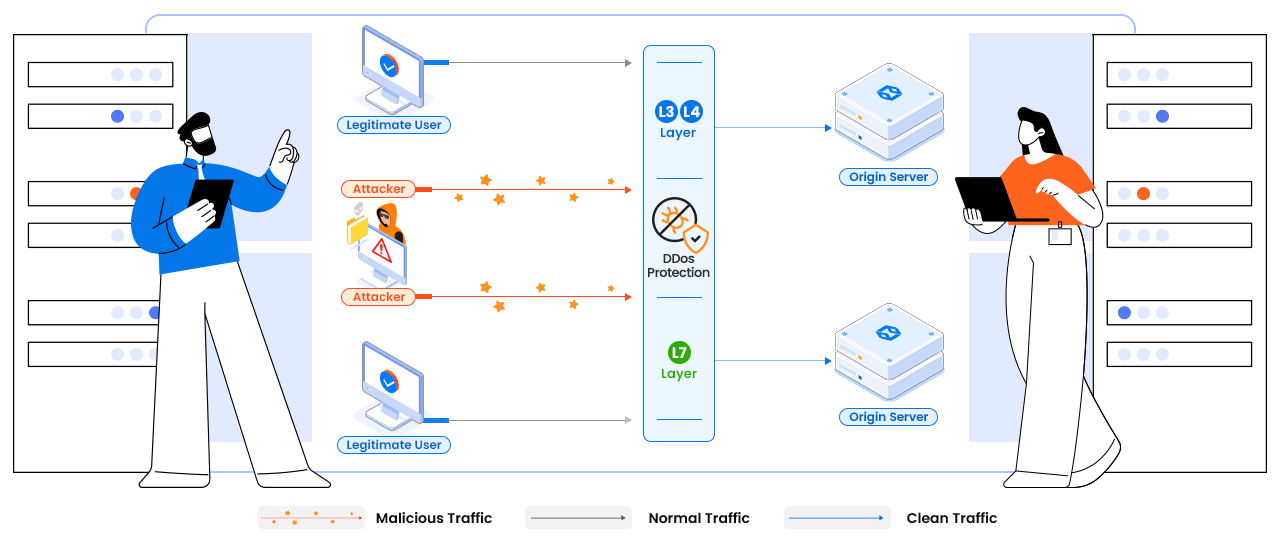
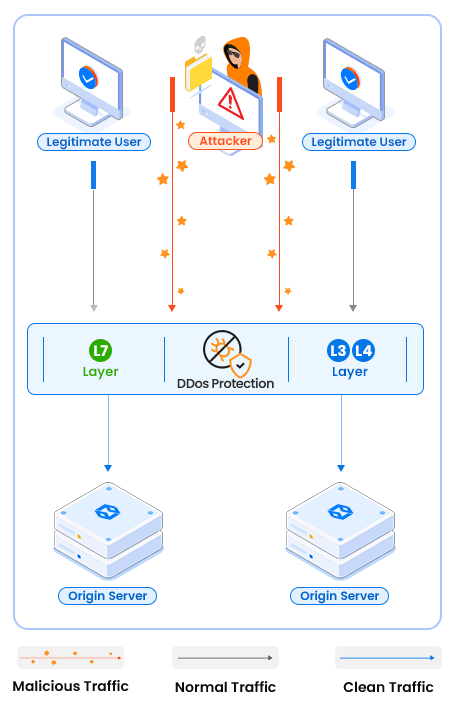

Proactive DDoS ProtectionOur DDoS Protection service provides robust and reliable defense for your dedicated server. Our system is designed for constant monitoring and filtering, ensuring immediate detection and mitigation of potential threats before they impact your server’s performance.

Automated Threat Detection & RedirectionOur system continuously monitors network traffic, automatically detecting potential DDoS threats in real time. Upon detection, malicious traffic is immediately and automatically redirected to our strategically located overseas scrubbing centers. This automated process ensures rapid response and minimizes the impact of attacks on your server’s availability and performance.

Granular Traffic FilteringWithin our scrubbing centers, a multi-layered system performs granular traffic filtering. This filtering is based on a variety of factors, including IP addresses, ports, and protocols. This precise filtering ensures that only legitimate traffic is allowed to reach your server, preventing false positives and ensuring that genuine visitors are never blocked.

Seamless Traffic DeliveryAfter malicious traffic is identified and removed, the clean, legitimate traffic is seamlessly forwarded to your server. This process happens in the background, ensuring minimal latency and no noticeable interruptions to your server’s operation. Your server continues to operate optimally, providing a consistent and reliable experience for your users.

Continuous Threat Intelligence & AdaptationOur team of security experts continuously analyzes the latest DDoS attack patterns and exploits. This information is used to constantly update our DDoS protection system, ensuring that it remains effective against even the most sophisticated and evolving threats. This proactive approach ensures your server is always protected against the latest attacks.
Types of DDoS Attacks We Protect Against
UDP attacks
- UDP Flood
- IP Fragmentation
- VoIP Flood
- Media Data Flood
- Non-Spoofed UDP Flood
TCP attacks
- SYN Flood
- SYN+ACK Flood
- ACK & PUSH ACK Flood
- Fragmented ACK
- RST or FIN Flood
- Synonymous Flood
- Fake Session
- Session Attack
- Misused Application
ICMP attacks
- ICMP Flood
- ICMP Fragmentation
- Ping Flood
- Fragmented ACK
- RST or FIN Flood
- Synonymous Flood
- Fake Session
- Session Attack
- Misused Application
In-Demand Use Cases
- Protecting Transactions:
Ensures availability and integrity of payment gateways and trading platforms, preventing financial losses and regulatory penalties. - Securing APIs:
Safeguards APIs from attacks, maintaining critical business processes. - Preventing Account Takeover:
Ensures security systems are available to prevent account breaches. - Maintaining Trading Platform Availability:
Guarantees continuous operation of high-frequency trading platforms.
- Maintaining Availability During Peak Seasons:
Ensures websites remain responsive during high-traffic periods, preventing lost sales. - Securing Payment Gateways:
Protects payment processing from disruption, maintaining sales. - Protecting Customer Data:
Ensures security system availability to safeguard sensitive information. - Maintaining Brand Reputation:
Prevents downtime to maintain a positive brand image.
- Preventing Game Server Downtime:
Ensures game server availability for uninterrupted gameplay. - Securing Game APIs:
Protects APIs from attacks, maintaining critical game functions. - Protecting Against Cheating:
Prevents attacks that create opportunities for exploits. - Maintaining Player Experience:
Ensures a positive gaming experience by preventing disruptions.
- Ensuring Service Availability:
Maintains continuous service operation to prevent revenue loss. - Protecting Customer Data:
Ensures security system availability to safeguard data. - Maintaining Uptime SLAs:
Helps meet customer uptime agreements. - Securing APIs:
Protects APIs from attacks, maintaining critical functions.
Let’s Talk About Protecting Your Business
As DDoS attacks become increasingly severe, implementing strong protection and mitigation strategies is essential.
By partnering with Dataplugs to manage DDoS threats, you can focus your resources—time, effort, and budget—on enhancing user satisfaction and growing your business.
By partnering with Dataplugs to manage DDoS threats, you can focus your resources—time, effort, and budget—on enhancing user satisfaction and growing your business.
Get in touch with our experts today to discover how you can connect to our stable, secure, and protected global network.

















